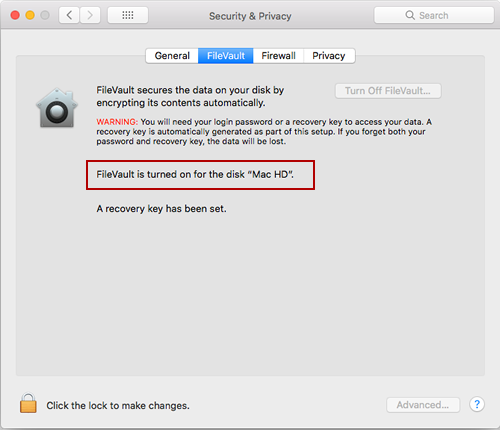
Encrypted Filesystem For Mac
To encrypt a drive, simply open the Finder and connect the drive to your Mac. Ctrl+click or right-click the drive in the Finder sidebar and select the Encrypt option. The disk will be encrypted once you enter your password of choice—be sure to use a secure one!
Formatting Your USB KeyTo start off with, you’re going to want to format your shiny new USB key. By default these things come pre-formatted using the MS-DOS (FAT32) filesystem as it is compatible under Mac OS X, Linux and Windows. If you want your USB key to work on most systems, I recommend using FAT32. The only FAT32 limitation that users should be aware of is that it only supports files as large as 4GB.
So if you plan on using it to copy DVD disk images, or other large files, you will want to either the file into multiple chunks, or use another filesystem (see below).The other filesystems you may want to consider are HFS+ (Mac OS X) or NTFS (NT Filesystem). Unfortunately, writing to NTFS partitions is not natively supported in Mac OS X, although a couple of projects exist that enable this (I recommend ).
Similarly, using an HFS+ partition will only be readable by Macs. There also exist one and one app that enables Windows to read/write HFS+ drives.To format your USB key, plug it in, open Disk Utility (/Applications/Utilities/), select it in the left-hand menu, then click on the Partition tab. Select ‘1 Partition’ from the Volume Scheme dropdown, and select ‘MS-DOS (FAT)’ in the Format dropdown. Click Apply (remember this will erase the USB stick). If you want to securely wipe the USB stick, see the section on.To those of you interested in installing a bootable OSX or Linux partition, you will want to consider partitioning the disk into two parts. For Linux I recommend about 2-3GB (FAT32), for Mac OS X you’ll need at least a 3GB partition (Mac OS Extended (Journaled)).
Those of you interested in installing OSX on your USB stick, it’s usually as easy as creating a partition, and then using the OSX install DVD to install onto that partition. This is where the crypto comes in. Should your USB drive get lost, stolen or by the US Department of Homeland Security, you’re going to want to make sure your data remains safe (although DHS will strongly encourage you to reveal your decryption key).
TrueCrypt allows the creation of encrypted disk images that will work on OSX, Linux and Windows. If you do not need a cross-platform disk image, OSX users can use built-in disk images.On my USB stick I chose to create a large encrypted disk image, as I’m probably going to want to encrypt most of my files.
Rotational motion physics study guide answers. Study of the kinematics of linear and rotational motion, it is highly recommended that several units precede this unit on rotational motion — particularly if AP Physics 1 is the irst course in physics for students. Osamu dazai, mazda b3000 engine, the pigman study guide answers, f6a engine specs, canon ir3225 user guide, ib sl math textbook 2nd edition If you ally craving such a referred Conceptual Physics Practice Page Rotational Motion Answers ebook that will provide you worth, acquire the totally best seller from us currently from several preferred. Address queries about rotational dynamics and torque on this interactive quiz to evaluate what you know. A printable worksheet is available to use. Created Date: 4:46:20 PM. Rotational Motion. Angular Displacement. Angular Velocity. Type of motion where an object starts at one point and moves t. Type of motion where an object 'spins in place'. A measure of the amount of radians that an object rotates thro. A speed of rotation measured in radians/second.

However, I recommend that you do leave some free space for quick transfers of non-sensitive data (or if a friend needs to stick something on your drive) and no giving them your password is not a solution.For the sake of argument let’s say you want to create a 2GB encrypted disk image. Start by opening TrueCrypt, click on “ Create Volume“, and then select the “ standard” volume button, and click Next. Click on “ Select File” and enter the name of your disk image at the prompt (make sure you’re saving the file on your mounted USB stick). You now have the option of selecting the encryption algorithm to be used with you disk image.
Unless you have a particular reason for doing so, I recommend sticking with AES. Note that if you do choose any combination of encryption algorithms, it will slow down the speed of your disk image, as files will have to be encrypted/decrypted twice or even three times. You can leave the hash algorithm (RIPEMD-160) as-is. At the next screen enter the preferred size of your disk image, in this example we chose 2GB, click Next again.On the next screen you will be asked to enter a password. The strength of your password will determine how secure your encrypted disk image will be.
If you were to use a password like “apple”, it wouldn’t matter if you used all encryption algorithms together in a random complicated combinations, your disk image would be cracked open by a dictionary attack in about 0.34 seconds. For those of you who haven’t read it, my article on has a section on.TrueCrypt also has the ability to use ‘‘ as additional keys needed to decrypt a disk image. A key file can be any file on your computer, MP3, PDF, ZIP. Preferably this should be a file that is not going to change, so don’t use some text file that you edit on a regular basis. As this disk image will reside on your USB drive, the keyfile will also need to be on the drive if you want to be able to mount this image whilst on the move.
It’s all good and well having a USB drive that you can put files on, even encrypt stuff. But you can do so much more. Due to the nature of portable drives, they’re commonly used in conjunction with systems that aren’t your primary computer.
In some cases, these may even be untrusted machines, or machines with reduced functionality. Portable applications are apps that have been modified to run off of portable drives, without the need for installation, and most do not leave any trace of the execution on the host machine.There are many different portable apps already, but you will need one copy of each app for every operating system you wish to run them on.Mac OS X portable apps can be found at and.A large repository of Windows-compatible portable apps can be found at. Safari/Firefox: In many cases you may find yourself using an untrusted computer where it is beneficial to run your own browser. It may also be useful for privacy reasons as the portable browsers stores no history or cache files on the local machine. KeyPass: This application, which exists in OSX, Windows and Linux flavors, is a password repository. It can be used to store a list of passwords which are encrypted.
If you keep the necessary versions handy on your USB drive, then you’ll be able to access your password no matter what system you’re on. TrueCrypt: A (windows) version of TrueCrypt exists, which will be necessary on machines where TrueCrypt hasn’t been installed.
Note: The portable version will require you to be logged in as an administrator. In Mac OS X, just copy TrueCrypt.app to the USB stick. Tunnelier (windows): allows you to SSH, SFTP and create SSH tunnels.
This can be handy if you’re on an untrusted machine/network where you want to connect back to your home network.: TorBrowser is an anonymizing browser which tunnels traffic over the network.For those of you who work in IT or InfoSec you may want to add a number of other standalone tools, for example portable Wireshark, FTP clients, that come in handy on a regular basis. Linux (power users)I chose to install Linux on my USB drive, as from a security perspective, Linux has the potential for coming in handy on almost all computers (especially PCs). I chose to install a copy of the distro that comes pre-installed with many security tools (if you need these), but in the end, any distro will do.